Prerequisites
In order to enable control tower you will need the following:
A new AWS Account and a user with administrator permissions. (We recommend using an IAM user with admin permissions rather than the root user)
infoThis account will become the root of your multi-account setup after enabling Control Tower.
Three(3) new unique email addresses for your logs, shared, and security (audit) accounts.
A KMS Key for encrypting Control Tower Resources with a suitable permissions policy (See Guide Below)
A home region selection where your Control Tower configuration will reside.
cautionYour home Region is the AWS Region in which you'll run most of your workloads or store most of your data. It cannot be changed after you've set up your AWS Control Tower landing zone. For more information about how to choose a home Region, see Administrative tips for landing zone setup.
KMS Key Creation
For more help setting up KMS see the AWS docs: Guidance for KMS keys
Navigate to KMS in your root AWS account using a user with permission to create KMS Keys
Ensure you are in your home region and click
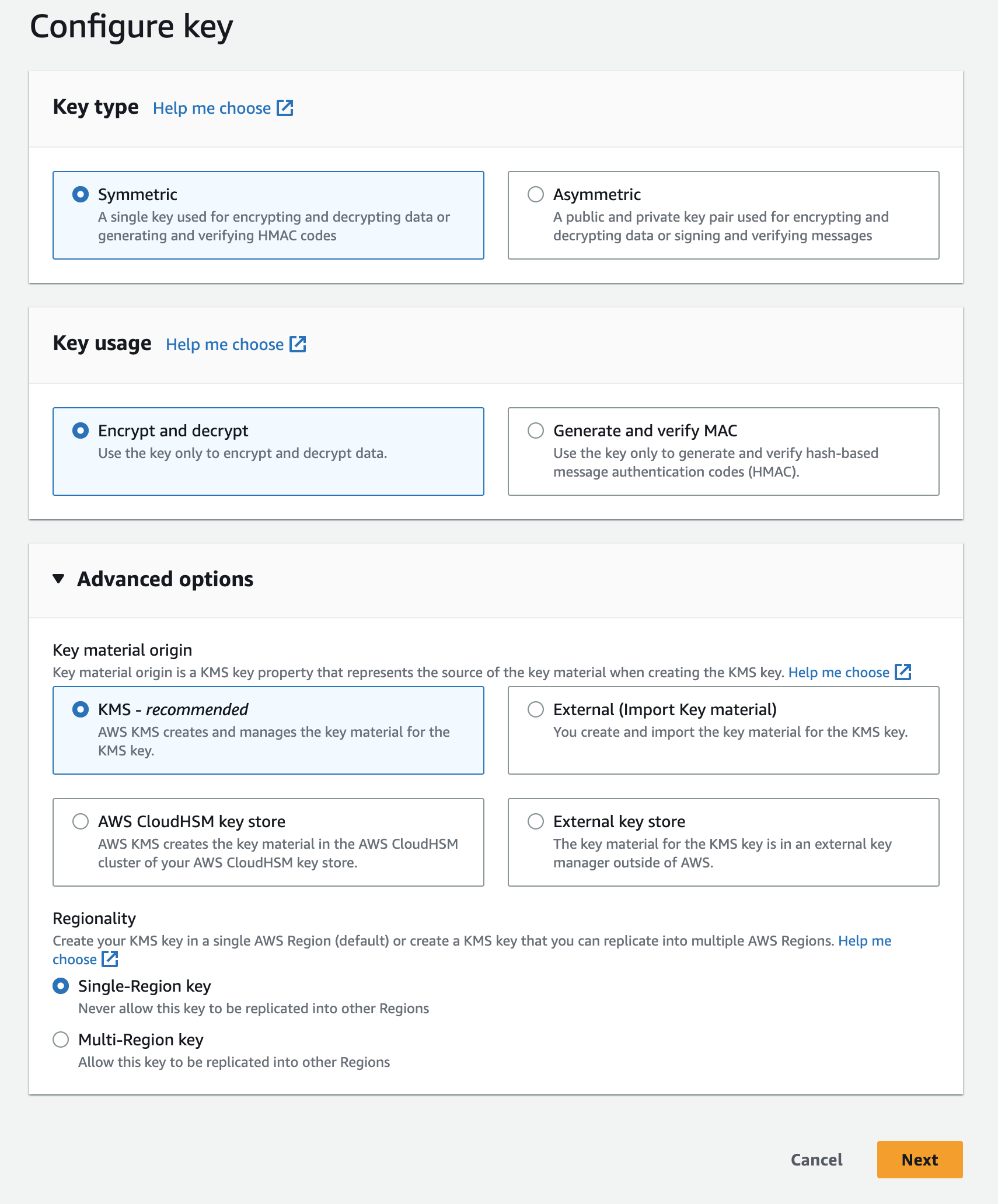
Create KeyConfigure a key with the default parameters (shown in screenshot below)
Give the key a descriptive alias like
control_tower_key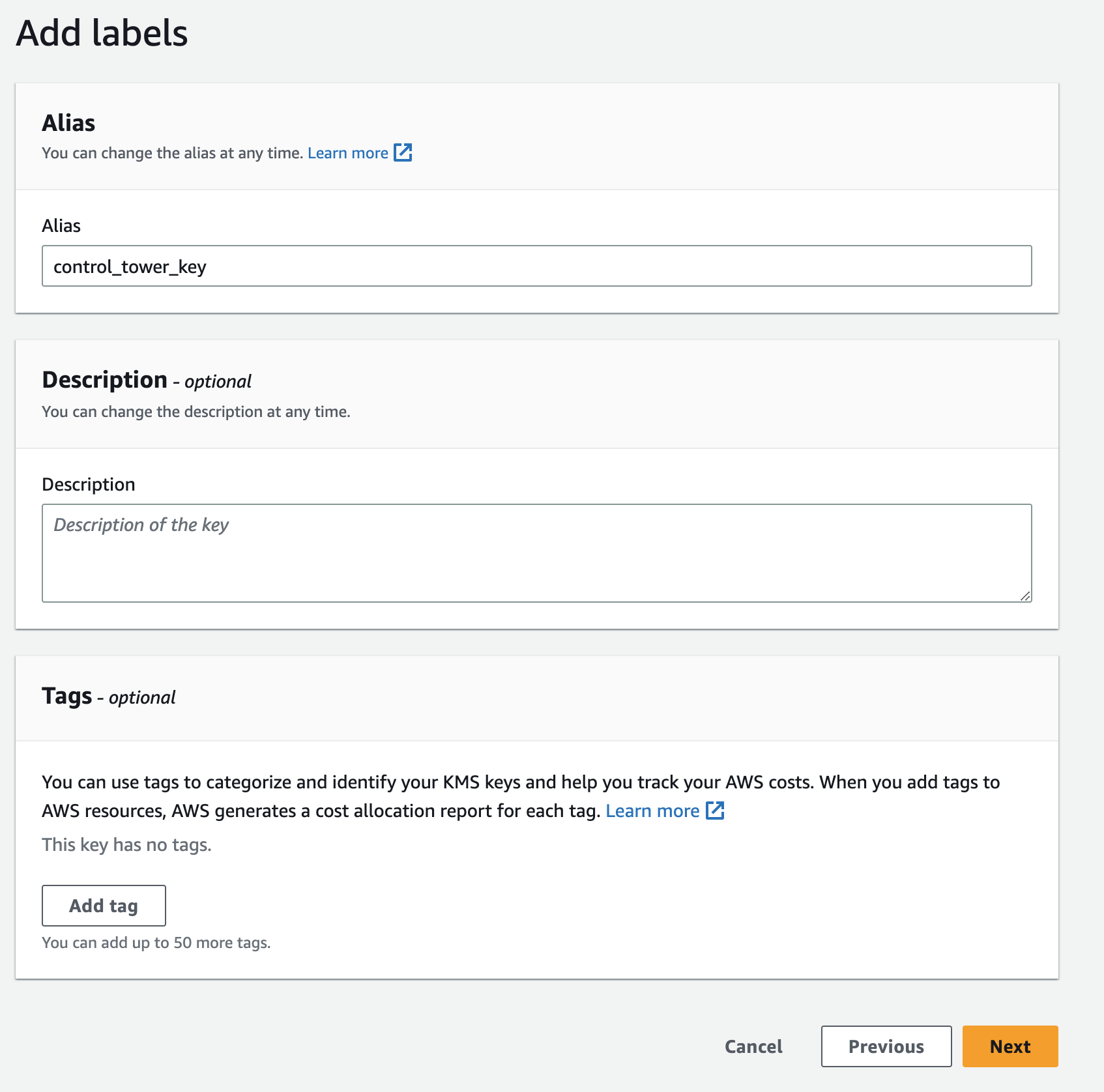
Select your admin user as a key administrator
Select your admin user as a key user
Click finish to create the key
On the next screen, find the key you just created and click on it to edit
In the key policy tab, click edit
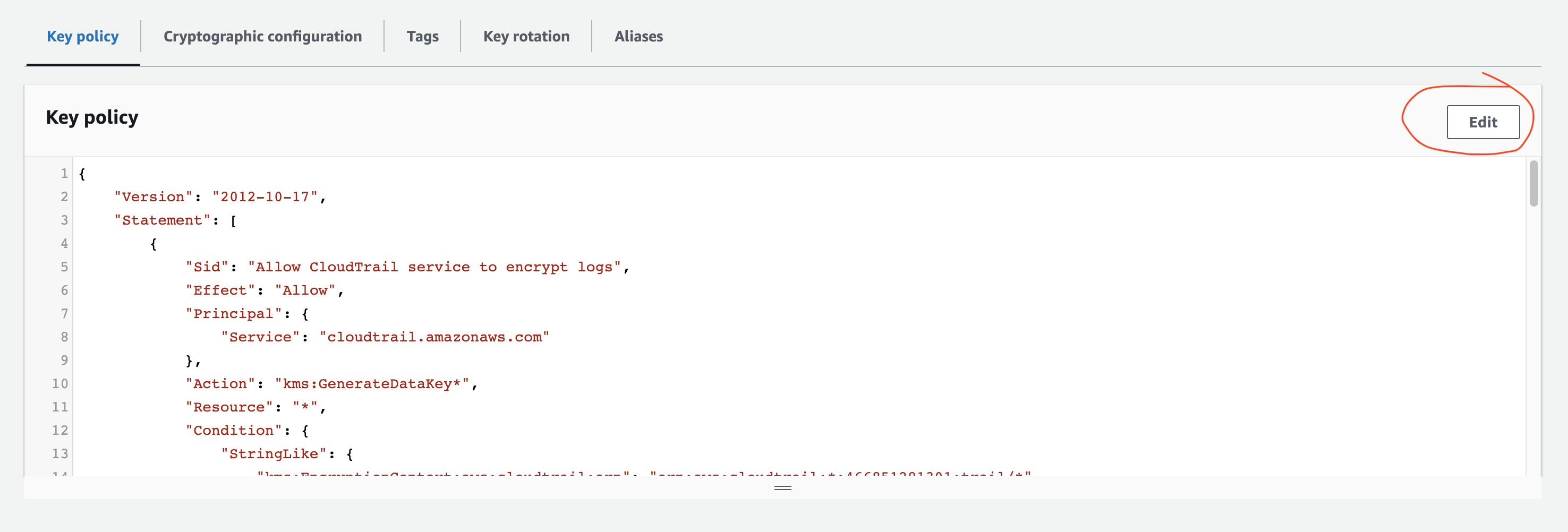
Add the following config policy statement to the list of Statements, replacing
YOUR-HOME-REGION,YOUR-MANAGEMENT-ACCOUNT-IDandYOUR_KMS_KEY_IDwith values from your own account.{
"Sid": "Allow Config to use KMS for encryption",
"Effect": "Allow",
"Principal": {
"Service": "config.amazonaws.com"
},
"Action": [
"kms:Decrypt",
"kms:GenerateDataKey"
],
"Resource": "arn:aws:kms:YOUR-HOME-REGION:YOUR-MANAGEMENT-ACCOUNT-ID:key/YOUR-KMS-KEY-ID"
}Add the following CloudTrail policy statement to the list of Statements, replacing
YOUR-HOME-REGION,YOUR-MANAGEMENT-ACCOUNT-IDandYOUR_KMS_KEY_IDwith values from your own account.{
"Sid": "Allow CloudTrail to use KMS for encryption",
"Effect": "Allow",
"Principal": {
"Service": "cloudtrail.amazonaws.com"
},
"Action": [
"kms:GenerateDataKey*",
"kms:Decrypt"
],
"Resource": "arn:aws:kms:YOUR-HOME-REGION:YOUR-MANAGEMENT-ACCOUNT-ID:key/YOUR-KMS-KEY-ID",
"Condition": {
"StringEquals": {
"aws:SourceArn": "arn:aws:cloudtrail:YOUR-HOME-REGION:YOUR-MANAGEMENT-ACCOUNT-ID:trail/aws-controltower-BaselineCloudTrail"
},
"StringLike": {
"kms:EncryptionContext:aws:cloudtrail:arn": "arn:aws:cloudtrail:*:YOUR-MANAGEMENT-ACCOUNT-ID:trail/*"
}
}
}Click
Save Changes